/ Amazon Web Services Insights, Blogs / By Saakshi Jaiswal
From ease of use to cost-effectiveness, security, and reliability, developing your IT infrastructure on AWS has many benefits. But every business has different goals and requirements, and to implement the technology, they need to understand the pros and cons of AWS offerings. That’s where an AWS well-architected framework steps in to help cloud architects build a better understanding and create a resilient and scalable architectural design.
What Is AWS Well-Architected Framework?
AWS’s Well-Architected Framework provides a consistent set of best practices to help businesses make the right decisions while building their systems on the cloud. Businesses can refer to these and evaluate how well their architecture aligns with AWS’s best practices.
The AWS reference architecture comprises the foundational questions based on the experience of thousands of customers. The goal of the AWS well-architected structure being simple – enable customers to measure the AWS architecture against best practices and address shortcomings.
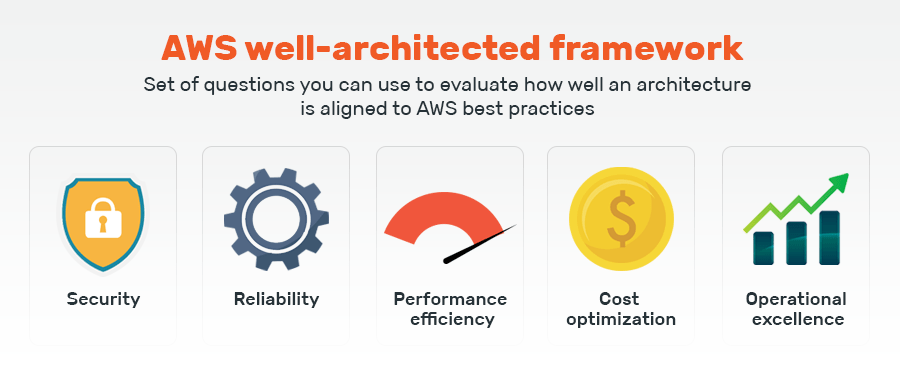
The 5 pillars of an AWS well-architected framework

Amazon solutions architect also defines the five pillars that lie at the core of the best practices laid down in the AWS reference architecture. Each of them further strengthens the concepts on which the technology is built.
1. Operational Excellence
Operational excellence refers to the enhanced ability to run systems and monitor operations for delivering business value. It also takes into account the continuous improvement of supporting processes and procedures.
The three actionable that complete the definition of Operation excellence in an AWS Well-Architected Framework are: Prepare, Operate, and Evolve.
- Prepare: The preparation step requires you to understand your workload. Having done that, you can then design and build the procedures to support your work.
- Operate: In this step, you define the metrics and measure operational outcomes against them. This will help you understand your operational health and identify where to improve.
- Evolve: Based on your operational health, the next step of achieving operational excellence lies in ‘evolution.’ You implement frequent small incremental changes based on your previous efforts in this step.
The Operational excellence pillar is what is used to derive the six design principles of an AWS architecture diagram:
- Perform operations as code
- Annotate documentation
- Make small, reversible changes
- Refine operations frequently
- Anticipate failure
- Learn and document outcomes, even failures
2. Security
This pillar refers to safeguarding systems, information, and assets using risk assessment and mitigation to help securely achieve business value. The security pillar of an AWS architecture includes identity and access management, detective controls, infrastructure protection, data protection, and incident response.
- Identity and access management: Critical for data and information security, identity and access management ensures that only authorized and authenticated users have access to your information and resources, just as much as intended and approved by you.
- Detective controls: An essential part of the governance framework; detective controls can be used for identifying potential security threats. Any anomalous activity while setting up the AWS architecture can be investigated using these controls.
- Infrastructure protection: Encompassing a set of methodologies, infrastructure protection ensures that your systems and services are safe from unintended, unauthorized access and guard against potential vulnerabilities.
- Data protection: Data classification, encryption, protection of data at rest as well as in transition, data recovery, and any other possible measure that protects data from theft or loss is included in the purview of data protection.
- Incident response: You aren’t completely risk-free, even with tight governance and security. Having incident response management in place ensures that if a security incident occurs, it does not affect the ability of your teams to operate efficiently. Additionally, it helps mitigate the effect of that incidence.
The design principles hence derived from the security pillar in an AWS architecture diagram are as follows:
- Build a strong identity foundation and define access rules
- Create traceability
- Automate security
- Protect data in transit and at rest
- Prepare for security events
3. Cost-Optimization
For every business, cost optimization can make a huge difference to the bottom line. This pillar in the AWS well-architected checklist is the foundation for removing all practices that add unnecessary costs or suboptimal resources, benefiting the business.
The best practices laid down by Amazon solutions architects in the AWS well-architected framework help businesses build processes without worrying about resources. It helps them achieve this by utilizing cost-effective resources, matching supply with demand, expenditure awareness, and continually optimizing over time.
- Utilizing cost-effective resources: Comprises right-sizing, appropriate provisioning, managed services, careful geographic selection, and purchase options that suit your business needs.
- Matching supply with demand: Moving to the cloud has one big advantage – you pay only for what you require. When IT service supply matches the demand when needed, you don’t need to waste your resources on overprovisioning.
- Expenditure awareness: You need to identify your cost drivers to set benchmarks to optimize expenditure. The cost can be considerably reduced (and curbed from being wasted) once you correctly attribute resource costs to the systems, individual businesses, or product owners. Accurate cost attribution allows you to identify profitable business units and products and allocate resources intelligently.
- Optimizing over time: Measuring and monitoring cost-optimization metrics can help you discover how large or less your resource utilization gap is. Continuously reducing this gap will make you more and more cost-effective over time.
This pillar serves as an AWS well-architected framework tool to derive the following design principles:
- Work out a consumption model
- Measure overall cost efficiency
- Don’t waste money and resources on data center operations
- Analyze expenditure and allocate to profitable business units
- Reduce the cost of ownership
4. Reliability
The pillar of reliability encompasses practices enabling a system to recover from disruptions, make available computing resources to meet service demand and address misconfigurations or transient network issues in the AWS architecture.
At the core of reliability’s definition is serviceability. By definition, service availability reduces when the application isn’t operating normally because of scheduled or unscheduled interruptions. To measure and improve availability, you first need to understand system dependencies with the help of an AWS solution architect associate.
It is also just as important to consider the cost of availability under this pillar. Designing applications for higher levels of availability spell additional costs. Therefore, you need to first analyze and identify your exact availability needs before embarking on application design.
The design principles hence derived from the security pillar are as follows:
- Test your recovery procedures in case of interruptions,
- Increase aggregate system availability,
- Measure the cost of designing an application with high availability levels,
- Don’t guess capacity.
5. Performance Efficiency
This pillar emphasizes efficiently utilizing computing resources to meet business requirements. It also establishes practices to maintain that efficiency as your business scales, demands grow, and technologies evolve.
The four main components of performance efficiency in an AWS architecture diagram include selection, review, monitoring, and trade-offs.
- Selection: Selecting the optimal solution for your business depends on the kind of workload involved. This optimal solution is often a mix of approaches to help improve business performance, such as request-response, event-driven, extract, pipeline, etc.
- Review: Initially, when you implement your first AWS architecture solution, you have limited choices. However, it becomes easier to adopt new features and experiment with time. Reviewing the results of your previous architecture and new ones shows how you are progressing. For example, you can use visualization techniques to identify performance issues, hot spots, and low utilization areas.
- Monitoring: After implementing your architecture, you need to continuously monitor it for performance and take corrective actions when problems arise. Corrective measures need to be quickly deployed so that you can resolve problems before your customers are aware of them.
- Trade-offs: An AWS solution architect associate will always keep trade-offs in mind. You can set up the framework for trade durability versus time to suit your business needs and deliver higher performance.
The design principles hence derived from the security pillar are as follows:
- Experiment often
- Have performance metrics in place
- Focus on going global as you evolve
- Use serverless architectures
Choosing The Right AWS Solution Architect Associate For Your Business
For any business looking to set up a cloud-based architecture, balancing all five pillars is impossible. You have to make a choice that’s best suited for you. However, identifying what you can trade off requires a deep analysis that only an expert partner can help you with.
Rapyder is a partner that you can rely on for your architectural solution. By evaluating your current business needs, understanding your current architecture, and predicting your future requirements, Rapyder helps craft winning solutions. But that’s not all; as an expert Amazon solutions architect, Rapyder also educates clients about the key elements of an AWS Well-Architected Framework and how to:
- Lower or mitigate risks before they happen
- Leverage best practices
- Create a consistent approach to reviewing architectures
- Focus on value-adding features, not firefighting
- Influence future architecture and more
For more about Rapyder and how it helps you take your infrastructure swiftly and smoothly to the cloud, look at our services or get in touch with our experts.




